In this class, you will learn how to use FortiEDR to protect your endpoints against advanced attacks with real-time orchestrated incident response functionality. You will also explore FortiEDR features and how they protect your endpoints automatically in real time.
Product Versions:
- FortiEDR 5.0
Exam:
- This course prepares you for the Fortinet NSE 5 – FortiEDR 5.0 exam.
Associated Certifications:
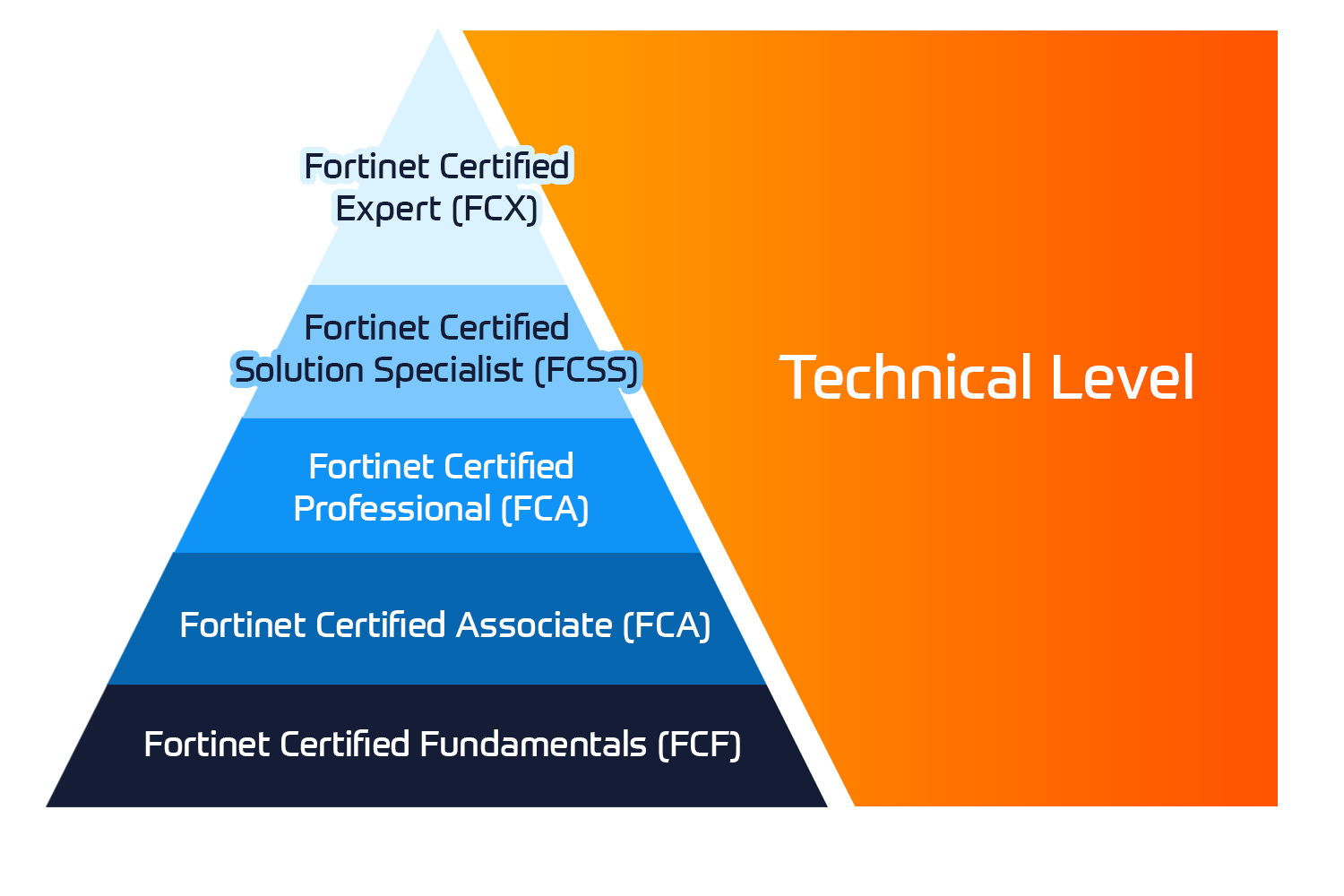
- Fortinet Certified Professional (FCP): Security Operations (Part of Elective Exams) *click for more details
Please note:
- This course is delivered by the Fortinet team.

 United Kingdom
United Kingdom Germany
Germany Denmark
Denmark Sweden
Sweden Italy
Italy Netherlands
Netherlands Norway
Norway 
















 Kesto
Kesto  Toimitus
Toimitus  Hinta
Hinta