Kehitä taitojasi
Tutustu laajaan valikoimaamme akkreditoituja ja toimittajista riippumattomia kurssejamme
Tuotamme ja tarjoamme globaalin huipputason koulutuspalveluita
Cisco-koulutukset
Tarjoamme täyden valikoiman virallisia Cisco-sertifikaatteja ja erikoisosaajatason teknologiakoulutuksia
Lue lisääFortinet-koulutukset
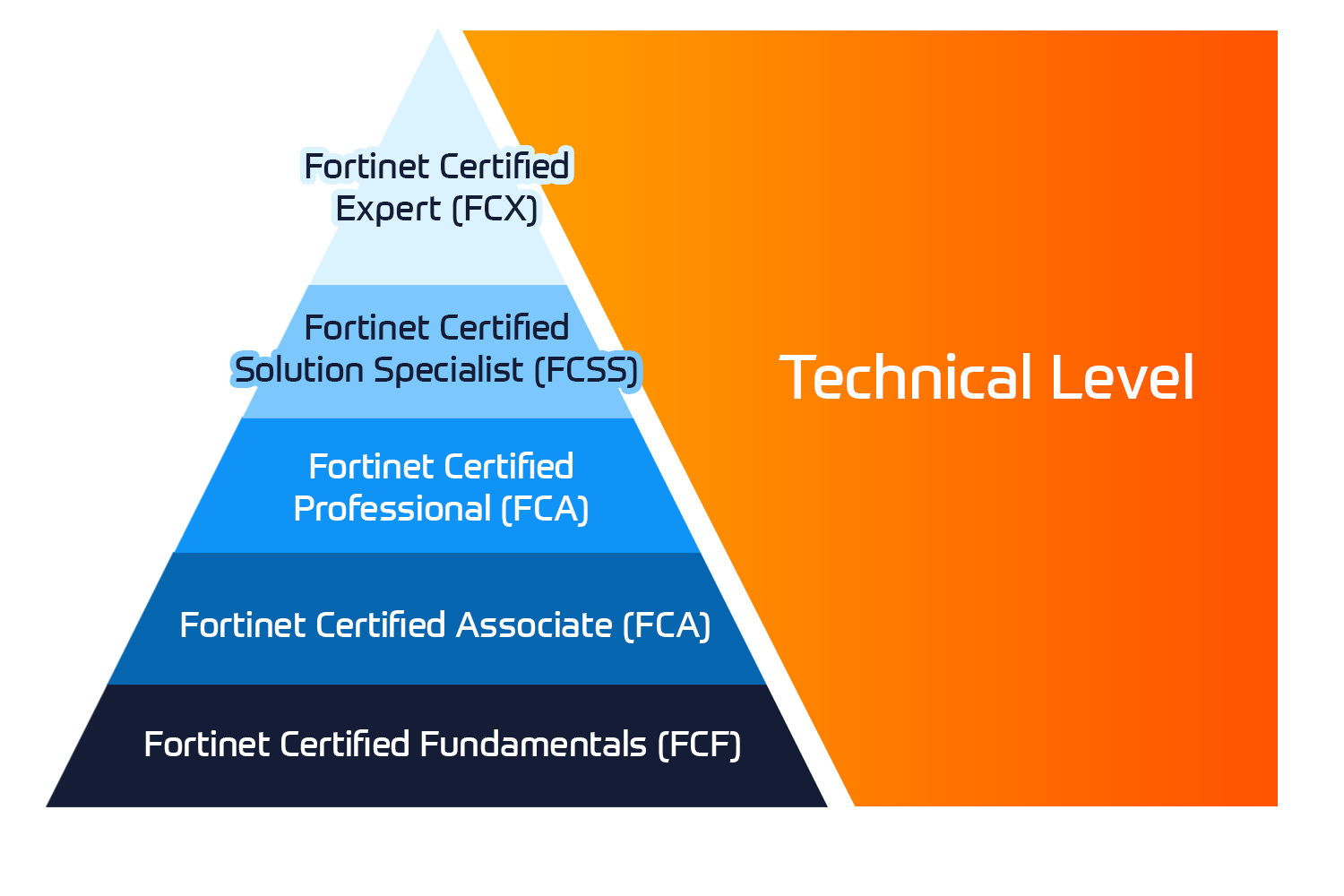
Olemme auktorisoitu Fortinet-kouluttaja ja tarjoamme koulutuksia kaikilta NSE-sertifiointitasoilta
Lue lisääExtreme Networks
Opi huippuluokan osaamista ja osallistu auktorisoituihin Extreme Network -koulutuksiin
Lue lisääMicrosoft-koulutukset
Räätälöimme sekä perus- että asiantuntijatason koulutuksia juuri sinun tarpeisiin sopivaksi
Lue lisää




Cisco-koulutukset
Tarjoamme täyden valikoiman virallisia Cisco-sertifikaatteja ja erikoisosaajatason teknologiakoulutuksia
Lue lisää
Fortinet-koulutukset
Olemme auktorisoitu Fortinet-kouluttaja ja tarjoamme koulutuksia kaikilta NSE-sertifiointitasoilta
Lue lisää
Extreme Networks
Opi huippuluokan osaamista ja osallistu auktorisoituihin Extreme Network -koulutuksiin
Lue lisää
Microsoft-koulutukset
Räätälöimme sekä perus- että asiantuntijatason koulutuksia juuri sinun tarpeisiin sopivaksi
Lue lisääOta yhteyttä meihin
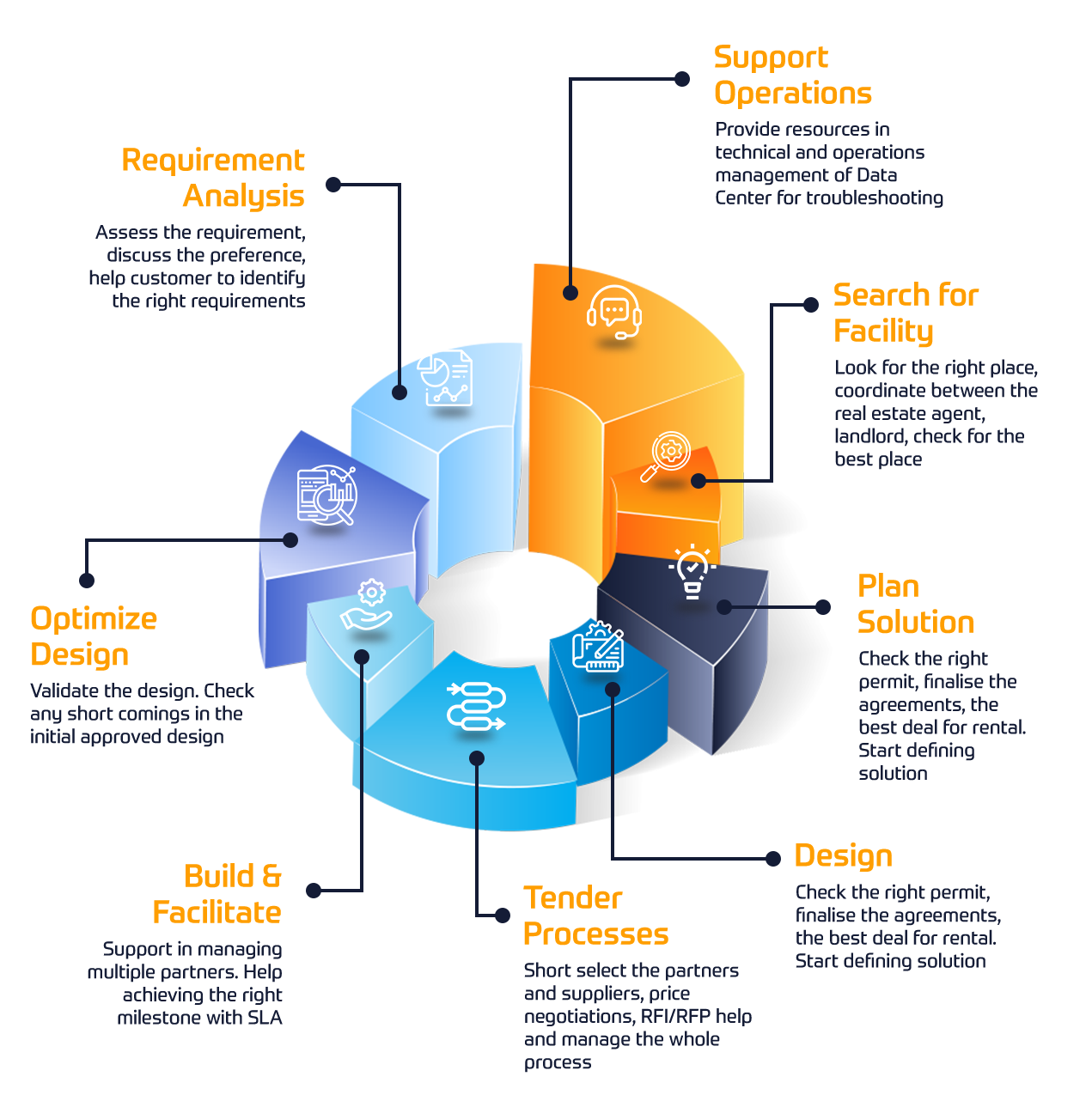
Olemme koonneet asiantuntijoista IP-verkkojen asiantuntijaryhmän ratkaisemaan klassisten IP-verkkojen siirtoon liittyviä haasteita.
Konsultointipalvelumme keskittyvät IP-pohjaisten verkkoratkaisujen kehittämiseen, siirtämiseen ja optimointiin käyttäen upouutta SDN-tekniikkaa.

Aloita opiskelu omaan tahtiin
Tutustu suosituimpiin verkko-oppimiskursseihimme: oppimisaiheita ovat esimerkiksi DevOps, verkkoautomaatio, kyberturvallisuus ja paljon muutaJoidenkin asiakkaidemme projektitiedotteet löytyvät täältä
















Insoft Service on johtanut vuodesta 2010 lähtien useita Juniper Networksin projekteja. Olemme tarjonneet asiantuntijapalveluita suoraan Katajalle sekä Juniper Networksin eri asiakkaille huippuosaamistason palvelukumppanina
Insoft on palvellut Fortinetin asiakkaita vuodesta 2014. Olemme suojanneet asiakasverkkoja palomuureja siirtämällä, Uudestaan käytäntöjä ja työskentelemällä viime aikoina FortiGate SD-WAN -alkuunpanojen parissa. Fortinet-konsultointipaketit tarjoavat kustannustehokkaan ja monipuolisen vaihtoehdon.

Palo Alton asiakkaiden tukeminen vaatii paljon lisää osaajia. Tuemme EMEA Labs -hankkeita säännöllisesti. Insoft Services hallinnoi Global Labs-infrastruktuuria, johon kuuluu paikkasidonnaiset ja virtuaaliset laitteet, jotka mukauttavat ja kopioivat kaikki kokoonpanot

Insoft Service on auttanut Teliaa monella tasolla Turun kaupungin Smart City -projekteissa, sekä auttanut Teliaa nostamaan osaamistasoaan ainakin 25:ssä projektissa monissa Pohjoismaissa.
Verkot kehittyvät, vai mitä?
Erikoistunut verkkoautomaatioon ja suurikokoisten Zero touch -käyttöönottojen käyttöönottoon

 United Kingdom
United Kingdom Germany
Germany Denmark
Denmark Sweden
Sweden Italy
Italy Netherlands
Netherlands Norway
Norway